INTRODUCTION
Through this data, financial resources are rotated in orderly and close rules. If the data and the intervention process were invalid, it will surely happen disruption and injury to business reputation and loss of that prestige enterprise.
By cooperation closely with other organizationsin the field of security systems well-knownin the world, our company ensures to provide customer solutions in the system security 06 level (theofficials and law, administration, trade, financial and human) with standards ofISO 27001: 2005 for10 elements (security policy, organization, classification and resource control, security, security and physical environment, managing demonstration and communication, access control, maintenance and improvement, continuous management, obey) may affect the securityof enterprise information3 Industry to ensure its properties: confidentiality, integrityand availability.

External Firewall
Intermediary security
This security is essential based on the basic security features of network devices, operating systems...... For example, with high-end network equipment we can deploy network security features as basic as:
- Access control list restrict access of end users through the area, theapplication not belong their access.
- Set up access via username and password
- Limit connectionsto the system (physical connection) at the location is not allowed through the port securityfeature, VLAN access control list of network devices.
-
VLAN Zoning restricts useless data (Broadcast, ARP signal...) filled fromthis area overother areas, take full advantage of bandwidth for useful information (the user's real traffic) of the system. Prevent the virus diffusion effect due to the unstable of the system hardware from these regions to other regions.
- Etc...
internal firewall
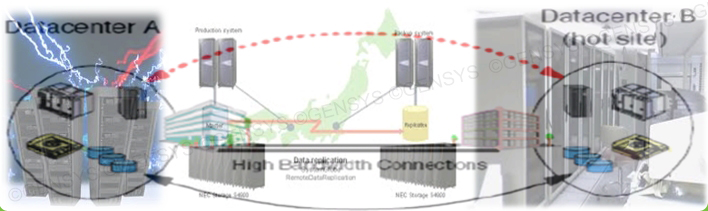
Subsystem internal firewall plays a very important role as the last security barricades to protectthe entire data system of enterprise. This subsystem also is the control gateway before it enters the most sensitive system, is the area of the central server. The special feature not only prevents the attacks fromthe outside environment into the system, the firewall device must also analyze all accessible from the LAN, filter and block the attacks comes from internal. Furthermore, the firewall device in this system is the kind of high handle capacity (throughput) and especially with high performance devices such as Intrusion Prevention System.

COMPREHENSIVE SECURITY SOLUTIONS
Comprehensive network security solutions include:
Network Security Solutions
- Firewall: Helps control network traffic based on established security rules. It prevents unwanted or dangerous connections.
- Intrusion Detection and Prevention System (IDS/IPS): Intrusion detection and prevention system helps monitor network traffic and detect suspicious or illegal activities.
- VPN (Virtual Private Network): Creates a secure and encrypted connection between users and the network system, protecting data when transmitted over public networks.
Data Security Solutions
- Encryption: Data is encrypted to protect against eavesdropping or changes when transmitted over the network or when stored.
- Data Loss Prevention (DLP): Helps prevent data loss by monitoring and controlling the flow of data in and out of the system, especially sensitive data.
- Data Backup: Ensure data is backed up regularly and can be restored when necessary after an incident.
Endpoint Security Solution
- Antivirus/Antimalware: Helps detect and remove malware and viruses that attack endpoints such as computers and phones.
- Endpoint Detection and Response (EDR): A solution that detects and responds to attacks on endpoints, helping to prevent threats in a timely manner.
Identity and Access Management (IAM) Solution
- Multi-Factor Authentication (MFA): Uses multiple layers of authentication to protect access to the system.
- Access Control: Ensures that only authorized users can access important resources, by setting up role-based access rules.
- Single Sign-On (SSO): Allows users to access multiple applications and systems with just one login, making identity management and security easier.
Application Security Solutions
- Vulnerability Management: Regularly check and fix vulnerabilities in software and systems.
- Web Application Firewall (WAF): Helps protect web applications from common attacks such as SQL Injection, Cross-Site Scripting (XSS), etc.
- API Security: Control and protect API connections between applications to avoid external risks.
Monitoring and Response Solutions
- Security Information and Event Management (SIEM): A system that collects and analyzes data from various sources in the network to detect threats and alert on unusual events.
- Security Operations Center (SOC): Security monitoring center, where security experts manage and respond to cybersecurity incidents 24/7.
- Incident Response Plan (IRP): A plan to respond when a security incident occurs, including steps to fix and restore data and systems after an attack.
Training and Awareness
- Human resource training: Help employees understand cybersecurity risks, such as phishing attacks, malware, and know how to respond properly.
- Strengthen businesses to build security policies (Security Policy): Build and apply clear internal security policies, including regulations on device use, data access, and incident response.
Security Testing and Auditing
- Penetration Testing: Conducting tests to find vulnerabilities in network systems and applications by simulating real-world attacks.
- Audit: Periodically evaluate security measures, processes, and policies to ensure compliance with security standards.
Protection against advanced cyberattacks
- Advanced Persistent Threat (APT) Protection: Protection against targeted, long-term attacks, often carried out by sophisticated criminal organizations.
- Artificial Intelligence and Machine Learning (AI/ML): Apply AI and machine learning to detect and predict new security threats.
With many years experience in the field of network security, our company commit to provide a full comprehensive security solution to minimize the possiblerisk to the system of enterprise’s computer networks. Solutions built withdevice leading security vendors as Fortinet, Watchguard,Astaro ... from basic to integrate many levels of security - including firewall, antivirus, intrusionprevention in, VPN,web content filtering, spyware prevention andanti spam - designed to help customers protect against the potential risks at the level across the entire content of the systemfor small tobig businesses.
 SECURITY SYSTEM
SECURITY SYSTEM